In a data-driven world, data theft is not your only concern
| data | society | security | Time to read: 5 minuter (4903 tecken)
For most people, “IT security” is a cat and mouse game between hackers and security experts. Hackers want to steal information, while security experts try to stop the attempted thefts. But in reality, data integrity is often just as – or even more – important as making sure it’s not stolen.
High energy costs and smart heating #
During December, new price records have repeatedly been set on Nord Pool, “the leading power market in Europe”. The price peaked at just above 8 SEK per kWh between 5 and 6pm on December the 21st. But it fluctuates a lot. The lowest price during December was 0,2 SEK per kWh between 1 and 2am on December the 19th.
In the graphs below, bars are consumption per hour and the line shows the price per hour.
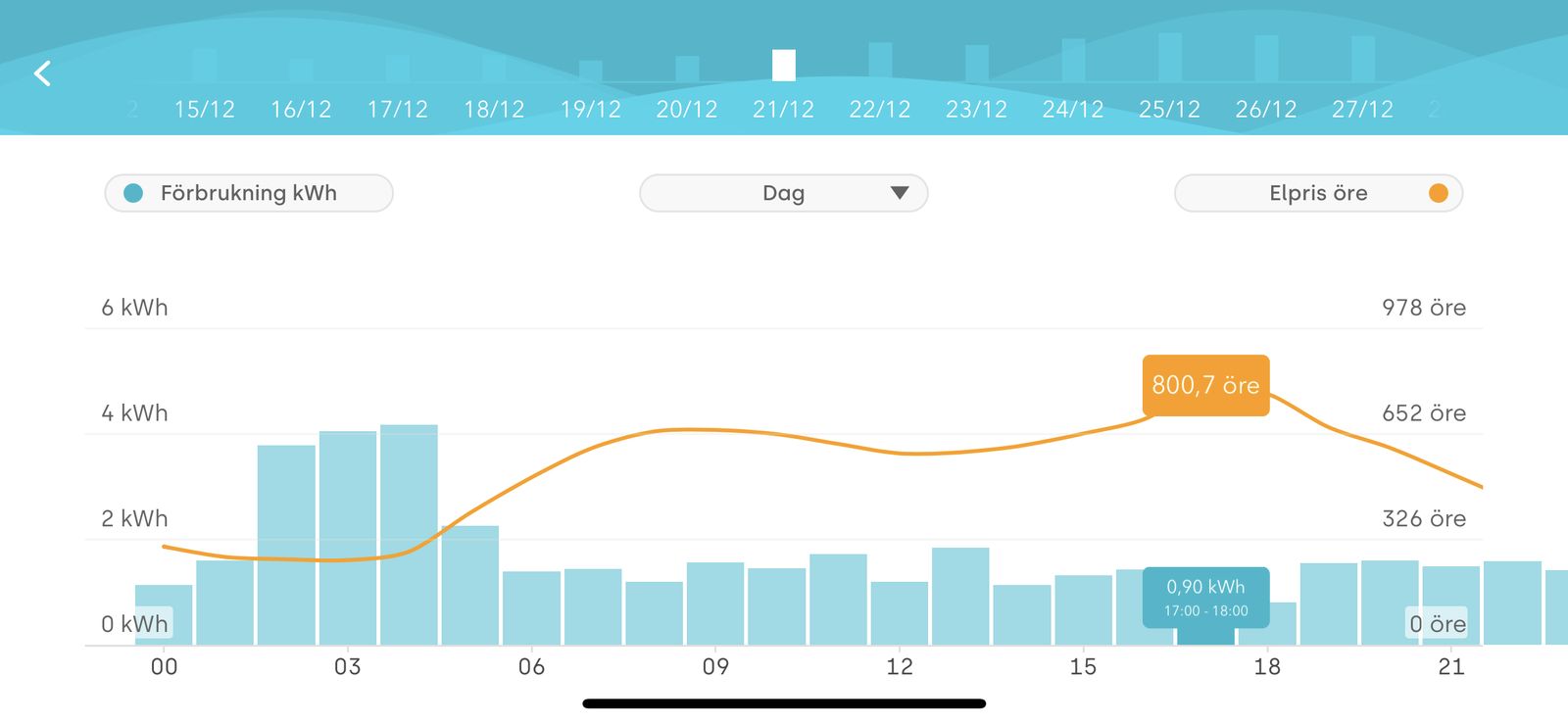
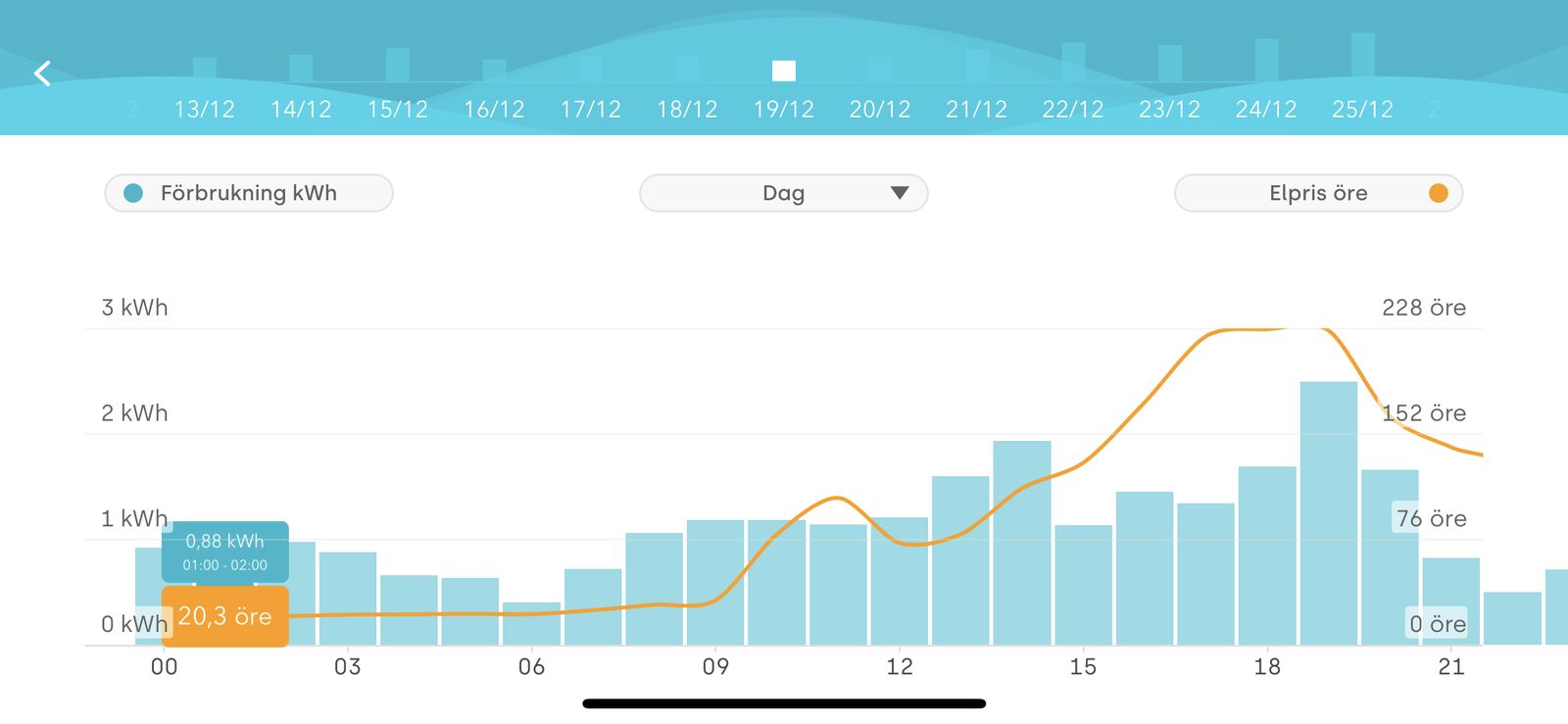
In my family’s home, the heating system is by far the biggest energy consumer. We buy our electricity from Tibber, paying the spot price on Nord Pool hour by hour. According to the statistics in the company’s app, heating accounts for 58 percent of our electricity use during December. But 58 percent of the energy consumption doesn’t mean 58 percent of the energy cost when you pay per hour.
Our heating pump has a feature called Smart Prive Adaptation. With that setting activated, the pump produces heat while prices are lower. This means that you can save a lot of money if you can offset your energy consumption to the cheapest hours as the pump did in the early morning of December 21st.
In the public debate, IT security is most often a question about protecting theft. For companies, making sure outsiders doesn’t get access to secret intellectual property. For individuals, protecting login credentials to their internet bank.
But in a world that is becoming increasingly data-driven, theft is not the only concern. There is no such thing as stealing the electricity price. I don’t know for sure, but shouldn’t our heating pump receive the current price I guess that it would just continue to run in “dumb mode”, heating our home as long as there is electricity in the grid.
But if someone manipulated the prices, tricking our heating system that cheap hours were the expensive ones, and the expensive hours the cheap ones, that someone could quickly run our electricity bill through the roof.
In a data-driven world, data integrity is extremely important.
Fake data and possible traffic incidents #
In 2020, German artist Simon Weckert did an art performance in Berlin. With 99 cellphones on a handcart, he walked through the city causing fake traffic jams in Google Maps. That so many cellphones moved that slow down the same streets caused Google’s algorithms to think that there was a traffic jam. Fake data fed into the algorithm had them make the wrong conclusion. But it turned out that there already was some resilience in Google's code: As soon as a car drove past Weckert and his cart, the algorithms understood that there was no traffic jam and the warning disappeared from the map.
While Simon Weckert’s work was a clever art performance, what Shir Yadid and Meital Ben-Sinai did in 2014 hints at possible practical implications. Yadid and Ben-Sinai, during that time software engineering students at Israel Institute of Technology, used simulated Android phones running the GPS application Waze. Having these simulated phones “move” slowly through the campus, they could create traffic jams on selected streets. Waze would pick up on those traffic jams, suggesting other routes. How could this be used?
- Create a simulated traffic jam.
- Have navigator systems suggest another route.
- Fewer cars and shorter travel time for those who know that the traffic jam is fake and choose to route others avoid.
With cars, there are other ways to influence what’s happening on the roads. Billboard hacking is when you hack large digital billboards, changing what’s displayed on the screen. A search for “hacked billboards” leads to stories about legit billboard messages replaced with porn (which happened outside Skellefteå in Sweden the day before New Year’s Eve), conspiracy theories, and other messages. Most of the time, the “audience” for the hacks is the humans passing by on the streets below.
But what if you don’t just use the billboard you’ve pwnd to display a funny or upsetting message? What if you use it to display something that looks totally innocent to the human eye, but that the algorithms in autonomous cars interpret as street signs or obstacles and act accordingly? If you do not have the skills to hack billboards, projecting images from drones is another option.
Make sure you can trust the data #
In the case of the fake traffic jams, a spokesperson from Google (who owns Waze) told 9to5Google:
Traffic data in Google Maps is refreshed continuously thanks to information from a variety of sources, including aggregated anonymized data from people who have location services turned on and contributions from the Google Maps community. We’ve launched the ability to distinguish between cars and motorcycles in several countries including India, Indonesia, and Egypt, though we haven’t quite cracked traveling by wagon. We appreciate seeing creative uses of Google Maps like this as it helps us make maps work better over time.
Checking, cleaning, and in other ways making sure data quality and data integrity is quickly becoming more important. And not only for data that are supposed to be kept as a secret.
If a system collects outdoor temperature, and that data is used for important decisions, making sure that the temperature readings in the database are correct is crucial even though the temperature itself is no secret.
If you are a data provider, theft is not your only concern. You also have to make sure someone isn’t tampering with your data. And if you are the user of data, making important decisions based on it, think about the probability of malicious data, what the effect could be, and how to mitigate the risks.
